The GEM Process
Big Idea Cases
Privacy-Preserving Blockchain Database
Newark NJ Pilot Case
Newark SNAP
Privacy-Preserving Blockchain Database
.png) Figure 1. Hased Personal Identifier
As shown in Figure 1 above, when we gather a data of Person A, A’s personal identifier dynamicly changes when a new data is added to A’s database. Since all the data is stored in a blockchain, when every new data block is added to the chain, the system generates a new hash index for the blockchain which becomes a hashed identifier for A. As an additional layer of security, we insert time blocks. These empty blocks are periodically added to the blockchain simply to alter the hased identifier even though no new data is added to the blockchain. Such an identifier will look meaningless and unmappable to any outsider since the value changes nearly every millisecond. Only the agency with limited access to the private blockchain could access to the original unhashed data. Thus only a limited group could trackback who owns each identifier.
2. Attribute Identifier (Partial Module 2)
Figure 1. Hased Personal Identifier
As shown in Figure 1 above, when we gather a data of Person A, A’s personal identifier dynamicly changes when a new data is added to A’s database. Since all the data is stored in a blockchain, when every new data block is added to the chain, the system generates a new hash index for the blockchain which becomes a hashed identifier for A. As an additional layer of security, we insert time blocks. These empty blocks are periodically added to the blockchain simply to alter the hased identifier even though no new data is added to the blockchain. Such an identifier will look meaningless and unmappable to any outsider since the value changes nearly every millisecond. Only the agency with limited access to the private blockchain could access to the original unhashed data. Thus only a limited group could trackback who owns each identifier.
2. Attribute Identifier (Partial Module 2)
.png) Figure 2. Hased Attribute Identifier
By using similar methodology based on the personal identifier, we also alter the attribute identifier that will also be stored on a blockchain. For example, if the data block for a personal credit score is accessed, when the time elapses the identifier associated with that data also changes. For example, the credit score for each individual is provided as a hash function. The decryption of this hash function is only accessible to a limited number of people who have the permission to access this data. An outsider may see the data, but only as a hash function that would not be useful for any fraudulent activities.
By utilizing a series of privacy-preserving modules to secure private information collected by GEM, we limit the access of information. This process makes it almost impossible for outsiders to access the GEM data. There can be more modules introduced into the system when any additional protection is needed. Our group is confident that we can use new technologies to secure the privacy of data whenever necessary.
Figure 2. Hased Attribute Identifier
By using similar methodology based on the personal identifier, we also alter the attribute identifier that will also be stored on a blockchain. For example, if the data block for a personal credit score is accessed, when the time elapses the identifier associated with that data also changes. For example, the credit score for each individual is provided as a hash function. The decryption of this hash function is only accessible to a limited number of people who have the permission to access this data. An outsider may see the data, but only as a hash function that would not be useful for any fraudulent activities.
By utilizing a series of privacy-preserving modules to secure private information collected by GEM, we limit the access of information. This process makes it almost impossible for outsiders to access the GEM data. There can be more modules introduced into the system when any additional protection is needed. Our group is confident that we can use new technologies to secure the privacy of data whenever necessary.
Newark NJ Pilot Case
Illustration: Imagineering GEM for Food Stamp Distribution
In 2016, Newark, the largest city in New Jersey recorded at least 12,960 children to be in extreme poverty. Also, one-third of New Jersey’s residents could not afford basic necessities of food. Poverty leads children to be in hunger, which is ironic since New Jersey is the fourth wealthiest state in the nation. Our goal for this example is to illustrate how GEM could help Food Stamp distribution to provide direct support for children who will be starving at this point as well.
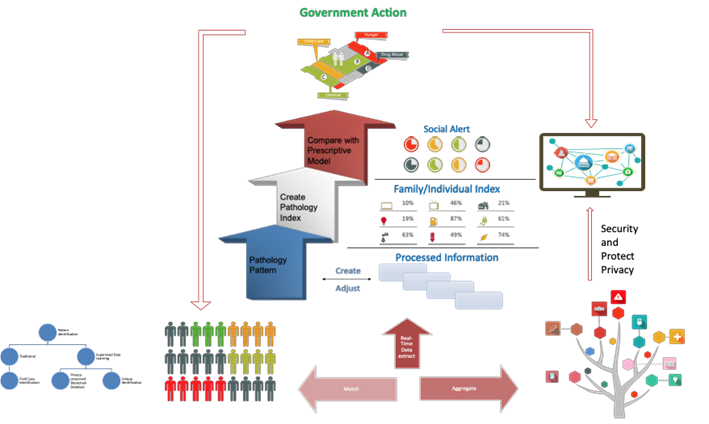
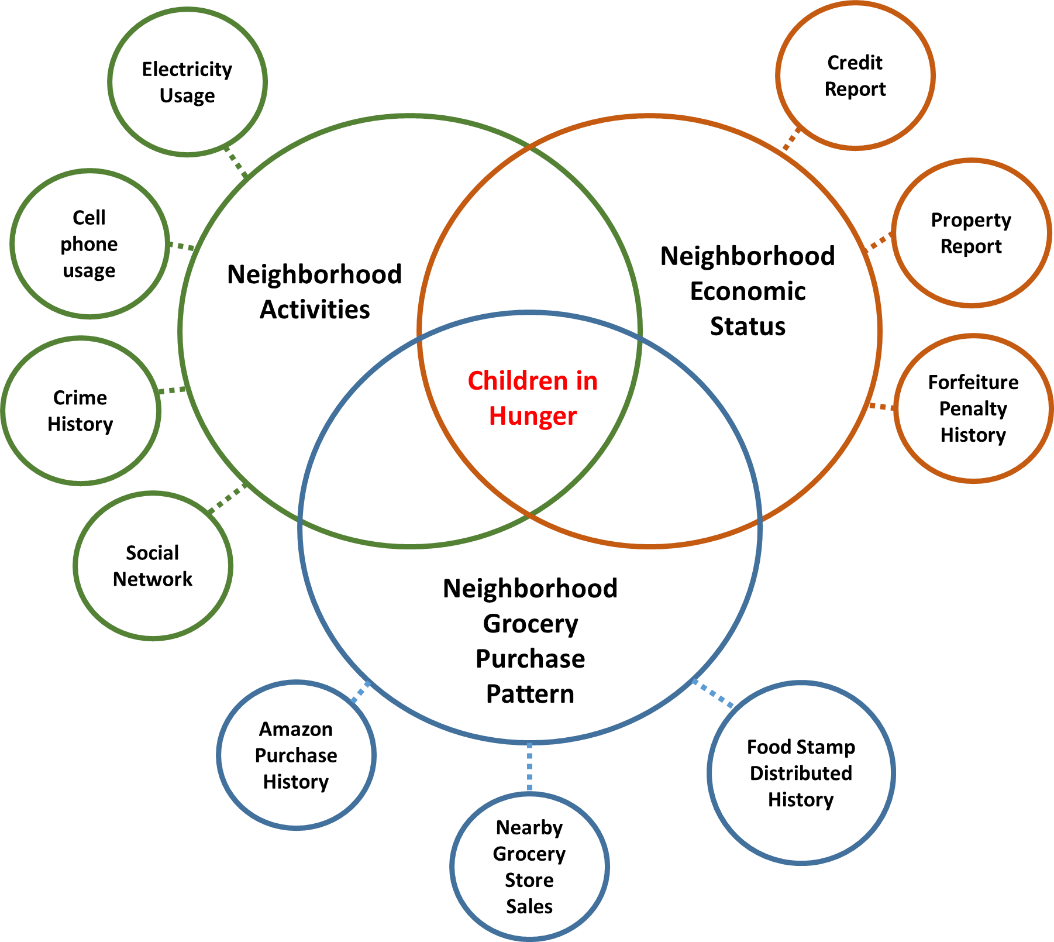 Figure 1. Data Collection
As provided in Figure 1, GEM first collects the data near the neighborhood related to poverty and hunger. For example, to find out poverty level in the neighborhood, we access to publicly available credit history, property report, forfeiture penalty reports, and any other necessary data. Based on this information, we conduct series of analysis to determine the neighborhood economic status while preserving personal privacy. In the other hand, we utilize the regional amazon purchase history, nearby grocery store sales data, and previous food stamp distributed history to find the neighborhood grocery purchase pattern. During data analysis, we heavily secure the data by using our proposed privacy-preserved blockchain database. Every input information provided by different institutions will be transformed into a hashed form where the data is stored in a blockchain which is visible only to permitted agencies. The security system will replace all the personal information into hashed indexes which changes every millisecond. This information will be highly secured in a private blockchain, however, even if this information be breached by any chance, there will be no mean to trace back the hashed index to individuals.
Figure 1. Data Collection
As provided in Figure 1, GEM first collects the data near the neighborhood related to poverty and hunger. For example, to find out poverty level in the neighborhood, we access to publicly available credit history, property report, forfeiture penalty reports, and any other necessary data. Based on this information, we conduct series of analysis to determine the neighborhood economic status while preserving personal privacy. In the other hand, we utilize the regional amazon purchase history, nearby grocery store sales data, and previous food stamp distributed history to find the neighborhood grocery purchase pattern. During data analysis, we heavily secure the data by using our proposed privacy-preserved blockchain database. Every input information provided by different institutions will be transformed into a hashed form where the data is stored in a blockchain which is visible only to permitted agencies. The security system will replace all the personal information into hashed indexes which changes every millisecond. This information will be highly secured in a private blockchain, however, even if this information be breached by any chance, there will be no mean to trace back the hashed index to individuals.
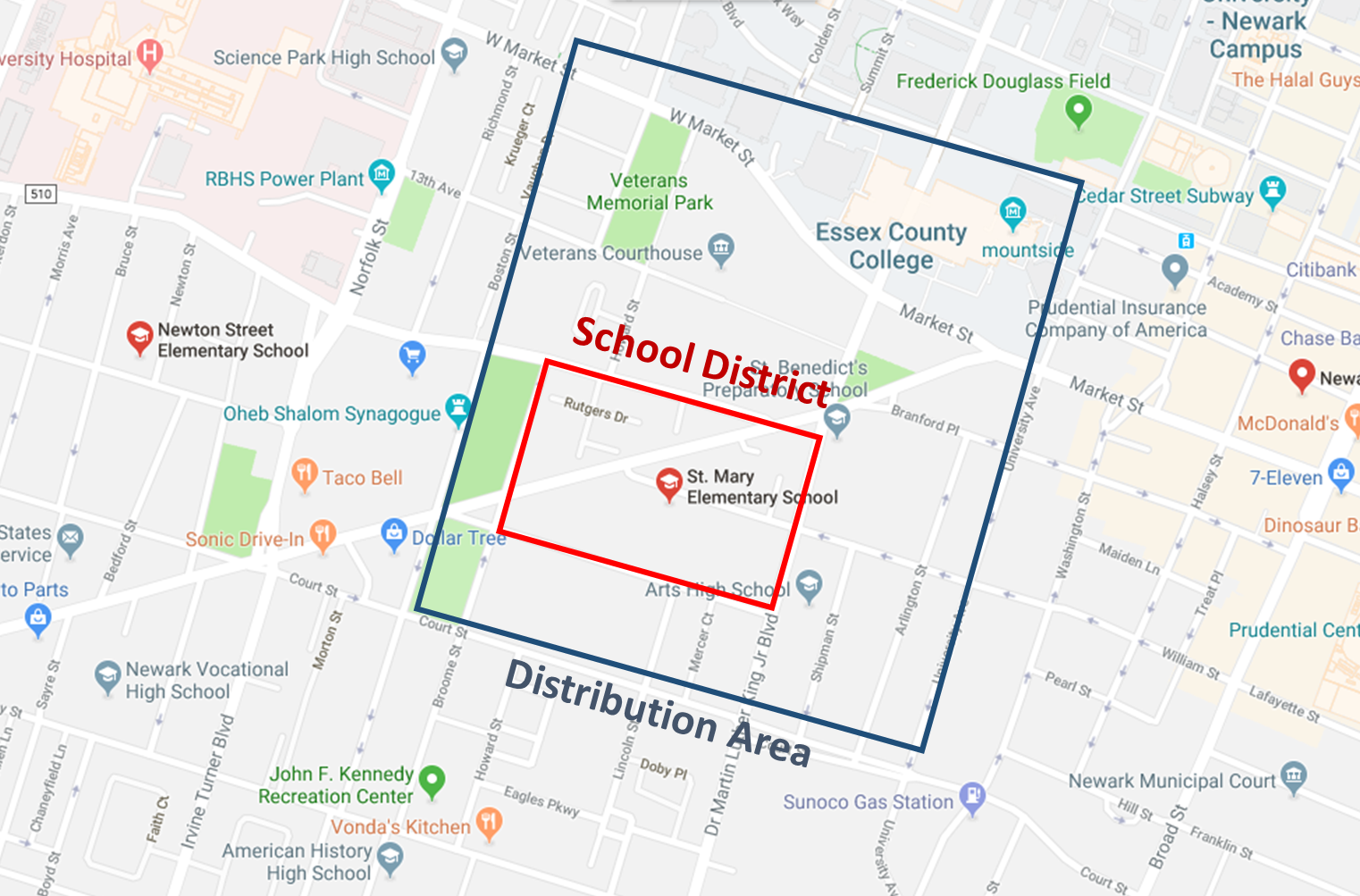 Figure 2. Food Stamp Distribution Area Suggestion
As well as considering the neighborhood activities, GEM provides the school districts where direct state actions are needed. On top of these results, the system suggests the area where the food stamp should have to be distributed. The system tracks the food stamp distribution history while keep monitoring to capture children in hunger in the neighborhood, it calculates the best timing for subsequent distribution. Therefore, the state could provide the food stamps to the children without any distribution gap. Moreover, when a state receives a request from the resident for food stamps, the system could provide evidence material which could assist the request review. Notably, the system will not utilize or provide any personal information which violates privacy.
Figure 2. Food Stamp Distribution Area Suggestion
As well as considering the neighborhood activities, GEM provides the school districts where direct state actions are needed. On top of these results, the system suggests the area where the food stamp should have to be distributed. The system tracks the food stamp distribution history while keep monitoring to capture children in hunger in the neighborhood, it calculates the best timing for subsequent distribution. Therefore, the state could provide the food stamps to the children without any distribution gap. Moreover, when a state receives a request from the resident for food stamps, the system could provide evidence material which could assist the request review. Notably, the system will not utilize or provide any personal information which violates privacy.
 Figure 1. Data Collection
As provided in Figure 1, GEM first collects the data near the neighborhood related to poverty and hunger. For example, to find out poverty level in the neighborhood, we access to publicly available credit history, property report, forfeiture penalty reports, and any other necessary data. Based on this information, we conduct series of analysis to determine the neighborhood economic status while preserving personal privacy. In the other hand, we utilize the regional amazon purchase history, nearby grocery store sales data, and previous food stamp distributed history to find the neighborhood grocery purchase pattern. During data analysis, we heavily secure the data by using our proposed privacy-preserved blockchain database. Every input information provided by different institutions will be transformed into a hashed form where the data is stored in a blockchain which is visible only to permitted agencies. The security system will replace all the personal information into hashed indexes which changes every millisecond. This information will be highly secured in a private blockchain, however, even if this information be breached by any chance, there will be no mean to trace back the hashed index to individuals.
Figure 1. Data Collection
As provided in Figure 1, GEM first collects the data near the neighborhood related to poverty and hunger. For example, to find out poverty level in the neighborhood, we access to publicly available credit history, property report, forfeiture penalty reports, and any other necessary data. Based on this information, we conduct series of analysis to determine the neighborhood economic status while preserving personal privacy. In the other hand, we utilize the regional amazon purchase history, nearby grocery store sales data, and previous food stamp distributed history to find the neighborhood grocery purchase pattern. During data analysis, we heavily secure the data by using our proposed privacy-preserved blockchain database. Every input information provided by different institutions will be transformed into a hashed form where the data is stored in a blockchain which is visible only to permitted agencies. The security system will replace all the personal information into hashed indexes which changes every millisecond. This information will be highly secured in a private blockchain, however, even if this information be breached by any chance, there will be no mean to trace back the hashed index to individuals.
 Figure 2. Food Stamp Distribution Area Suggestion
As well as considering the neighborhood activities, GEM provides the school districts where direct state actions are needed. On top of these results, the system suggests the area where the food stamp should have to be distributed. The system tracks the food stamp distribution history while keep monitoring to capture children in hunger in the neighborhood, it calculates the best timing for subsequent distribution. Therefore, the state could provide the food stamps to the children without any distribution gap. Moreover, when a state receives a request from the resident for food stamps, the system could provide evidence material which could assist the request review. Notably, the system will not utilize or provide any personal information which violates privacy.
Figure 2. Food Stamp Distribution Area Suggestion
As well as considering the neighborhood activities, GEM provides the school districts where direct state actions are needed. On top of these results, the system suggests the area where the food stamp should have to be distributed. The system tracks the food stamp distribution history while keep monitoring to capture children in hunger in the neighborhood, it calculates the best timing for subsequent distribution. Therefore, the state could provide the food stamps to the children without any distribution gap. Moreover, when a state receives a request from the resident for food stamps, the system could provide evidence material which could assist the request review. Notably, the system will not utilize or provide any personal information which violates privacy.
